The Hack of Cryptocurrency Payment Provider Explained: We Know Exactly How Attackers Stole and Laundered $37M USD

Being the world’s biggest crypto payments provider, it was essential for us to conduct a thorough investigation of the hacker attack of July 22nd, 2023, resulting in the theft of 37.3M USD. In collaboration with Match Systems, a top cybersecurity firm, we were able to trace the perpetrators’ steps minute by minute, as well as identify what services and platforms were used to launder the funds of our crypto payment gateway.
As promised, today, we are ready to reveal the details of the hack so that other providers in the crypto industry can learn from our experience.
Lazarus Hackers Linked to the Attack
Based on our internal investigation, we have reasons to suspect that the top-tier hacker group Lazarus may be behind the attack on the crypto payment gateway CoinsPaid. The hackers employed the same tactics and money laundering schemes that Lazarus had used in the recent Atomic Wallet heist.
Billed as the “top cyber threat groups around the globe in today’s time” by the media, the Lazarus Group is responsible for carrying out hacking campaigns all over the world, not just the CoinsPaid crypto payment gateway. Although the number of members and their names have not been identified conclusively, this cybercrime organisation is linked to the North Korean government.
From 2009-2013, “Operation Troy”, the first major attack attributed to Lazarus, took place and targeted government websites in the United States and South Korea.
In 2014, Lazarus saw global recognition for its Sony Pictures hack: the perpetrators released the company’s confidential documents, including information about employees, their work contracts and even their family members.
In 2017, almost ten years before the crypto payment gateway attack, Lazarus struck again: the WannaCry ransomware attack was a worldwide cyberattack in May 2017, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom in Bitcoin, showing Lazarus’ interest in crypto and bringing them closer to the future crypto payment gateway attack. The hack lasted 4 days and resulted in infecting 300,000+ computers worldwide.
As the crypto market and crypto payment gateway phenomenon gained more popularity and grew in capitalisation, the Lazarus Group began targeting numerous cryptocurrency platforms. The list of victims, as of today, amounts to over 20 companies, including Axie Infinity (USD 625M), Horizon Bridge (USD 100M), and Atomic Wallet (USD 100M).
There are many speculations regarding the long-term goals of Lazarus and the reasons for the growing frequency of attacks on enterprises, including our crypto payment gateway. Many experts believe the activities of the group to be an extension of North Korea’s desire to acquire foreign currency.
Hackers Spent 6 Months Tracking and Studying CoinsPaid
We now know that Lazarus, the supposed hacker group behind the attack, spent half a year trying to infiltrate the CoinsPaid systems and find vulnerabilities.
- Since March 2023, we have been registering constant unsuccessful attacks on the company of various kinds, ranging from social engineering to DDos and BruteForce.
- On March 27, 2023, key CoinsPaid engineers received requests from an allegedly Ukrainian crypto payment gateway startup with a list of questions regarding technical infrastructure, as confirmed by 3 major developers of the company.
- In April-May 2023, we experienced 4 major attacks on our systems aimed at gaining access to the accounts of CoinsPaid employees and crypto payment gateway customers. The spam and phishing activities against our team members were constant and highly aggressive.
- In June-July 2023, a malicious campaign was carried out involving bribing and fake-hiring critical company personnel.
- On July 7, 2023, a massive, carefully planned and prepared attack was executed targeting CoinsPaid crypto payment gateway infrastructure and applications. From 20:48 to 21:42, we registered unusually high network activity: over 150,000 different IP addresses were involved.
The perpetrators’ main goal was to trick a critical employee into installing software to gain remote control of a computer for the purpose of infiltrating and accessing CoinsPaid’s internal systems. After 6 months of failed attempts to break into the crypto payment gateway, the hackers managed to attack our infrastructure on July 22, 2023, successfully.
Social engineering — “the most dangerous” threat to security in 2023
Since it was not possible to hack CoinsPaid crypto payment gateway systems externally without gaining access to an employee’s computer, the attackers used highly sophisticated and vigorous social engineering techniques. Based on the Research by CS Hub results, 75% of cybersecurity specialists consider social engineering and phishing attacks the top threat when it comes to cybersecurity.
Fake Linkedin recruiting, bribing and manipulating employees
Recruiters from crypto companies contacted CoinsPaid employees via LinkedIn and various Messengers, offering very high salaries. For instance, some of our crypto payment gateway team members received job offers with compensation ranging from 16,000-24,000 USD a month. During the interview process, the perpetrators aimed to trick the candidates into installing the JumpCloud Agent or a special program to complete a technical task.
JumpCloud, a directory platform that allows enterprises such as a crypto payment gateway provider to authenticate, authorise and manage users and devices, was supposedly hacked by Lazarus Group in July 2023 in order to target its cryptocurrency users.
Although you may think that such an attempt to install malicious software on the employee’s computer is obvious, the hackers had spent 6 months learning all possible details about CoinsPaid, our crypto payment gateway, our team members, our company’s structure, and so on. Such top-tier hacking groups as Lazarus are able to create a completely believable story to take advantage of potential targets.
Tracing the Attack Step-by-Step
In the modern, highly digitalised world, it’s much easier to trick a person than computer software. By manipulating one of CoinsPaid’s employees, the hackers were able to attack the infrastructure of our crypto payment gateway our infrastructure successfully.
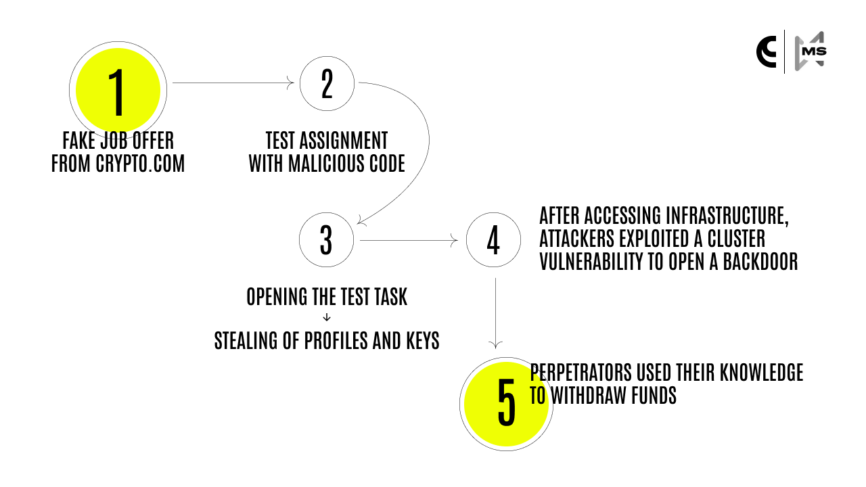
- One of our employees responded to a job offer from Crypto.com.
- While participating in the interview, they received a test assignment that required the installation of an application with malicious code.
- After opening the test task, profiles and keys were stolen from the computer to establish a connection with the infrastructure of the crypto payment gateway.
- Having gained access to the CoinsPaid infrastructure, the attackers took advantage of a vulnerability in the cluster and opened a backdoor.
- The knowledge perpetrators gained at the exploration stage of the crypto payment gateway enabled them to reproduce legitimate requests for interaction interfaces with the blockchain and withdraw the company’s funds from our operational storage vault.
In simple terms, the hackers gained access to the crypto payment gateway that allowed them to create authorised requests to withdraw funds from CoinsPaid hot wallets. Perceiving such requests as valid, they were sent to the blockchain for further processing. However, the perpetrators were not able to breach our hot wallets and acquire private keys to access funds directly.
Internal security measures triggered the alarm system of the crypto payment gateway and allowed us to swiftly stop the malicious activity and throw the hackers out of the company’s perimeter.
Blockchain Scoring Proves Ineffective Against Money Laundering
Although many crypto payment gateway and regular crypto companies employ KYC measures and use blockchain risk scoring systems to detect suspicious activity, the perpetrators still managed to launder the money successfully. Here’s why.
In line with standard procedure post any hacking event, CoinsPaid notified all major exchanges, crypto payment gateway providers, and cybersecurity firms of the incident, providing information about hackers’ addresses. They were then included in a markup, shared within the community, to prevent the further movement and laundering of the funds associated with these addresses.
However, distributing markup to subsequent addresses when moving stolen from the crypto payment gateway funds takes up to 60 minutes. Based on the results of our investigation, the CoinsPaid hackers moved funds to new addresses in a matter of minutes before the markup could keep up with the perpetrators’ actions.
This vulnerability makes blockchain scoring largely ineffective in preventing and minimising the impact of crypto payment gateway money laundering schemes employed by hacker groups in 2023.
The Money Trail: Tracing and Blocking the Stolen Funds
To aid with the investigation, CoinsPaid invited a partnership with Match Systems, a leader in cybersecurity that specialises in blockchain analytics and, in cooperation with law enforcement agencies and regulators, accompanies the process of returning crypto assets, stolen from crypto payment gateway providers and exchanges. Over $70,000,000 was recovered in several dozen criminal cases with the help of Match System specialists.
Immediately after the attack occurred, a set of operational measures to trace and potentially freeze the stolen funds were carried out.
Step 1. The hackers’ addresses were blacklisted on all major blockchain analyzers.
Step 2. Urgent notifications were sent to all major cryptocurrency exchanges, crypto payment gateway providers, and AML officers, informing them about the hacker’s addresses containing stolen assets.
Step 3. The hackers’ addresses were put on the Match Systems watchlist.
After taking the essential measures to increase the chance of temporary blocking of stolen crypto payment gateway funds, Match Systems’ specialists proceeded with the further tracing of the money trail via blockchain analyzers, native explorers and the firm’s own tools. An additional markup of the crypto payment gateway attacker’s addresses was carried out once the money passed through exchanges and swap services to see whether it had been moved cross-chain.
Majority of Funds Withdrawn to SwftSwap
As a result of the aforementioned steps, we were able to trace the stolen crypto payment gateway money fully. The majority of funds were withdrawn to the SwftSwap service in the form of USDT tokens on the Avalanche-C blockchain. After that, a portion of the funds was sent in the second round to the Ethereum blockchain, with a further transfer to the Avalanche and Bitcoin networks.
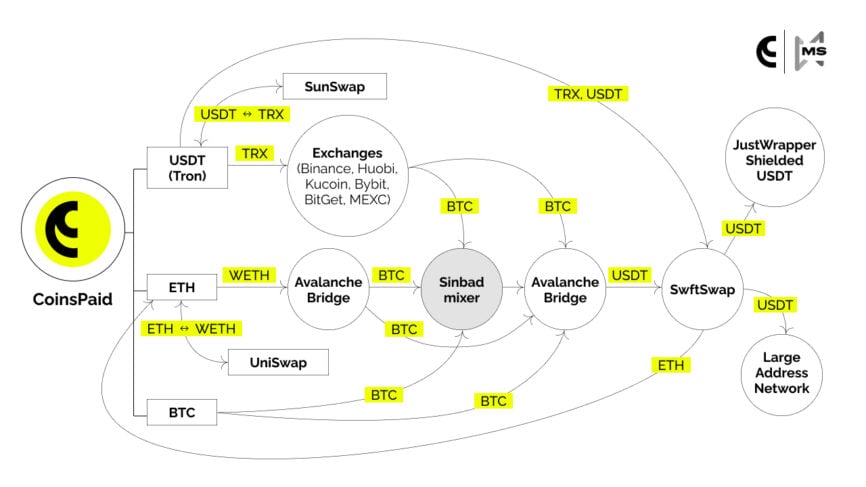
Indeed, a significant portion of the crypto payment gateway funds on SwftSwap was withdrawn to the addresses of the attacker with a large turnover. The same addresses were used to transfer stolen funds from the Atomic Wallet, giving us one more reason to believe that Lazarus may be responsible for the attack.
As of today, the crypto payment gateway money laundering activity of CoinsPaid hackers is ongoing, and we will continue to monitor the trail alongside Match System Specialists closely.
15% Lost on Fees and Volatility
Preliminary estimates show that a significant amount of the stolen funds was likely lost on the “operational costs” of the hackers.
- Up to 10% for a one-time exchange of a large number of crypto payment gateway tokens “on the market”: the seller collects most of the trades from the order book, resulting in significant price slippage. The most considerable losses occurred when hackers initially exchanged USDT for TRX.
- Up to 5% on commissions, discounts for the sale of crypto payment gateway tokens with a dubious history and other expenses. This also includes additional costs for purchasing accounts on exchanges and payment services, registered for “drops”, as well as hacking and remote administration programs.
Lazarus Hackers Used Similar Tactics in the Atomic Wallet Heist
Match System specialists discovered similar patterns on this crypto payment gateway heist that Lazarus previously used in their recent 100M USD Atomic Wallet hack.
1. Using the same swap services and mixers
Hackers utilised swap services, such as SunSwap, SwftSwap, and SimpleSwap, as well as Sinbad cryptocurrency mixer, to launder illegally obtained crypto payment gateway funds without any KYC and AML procedures.
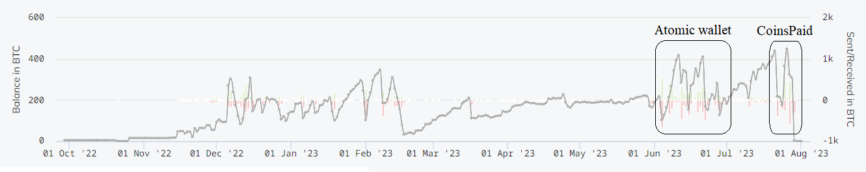
The Sinbad mixer volumes chart shows significant spikes in operations volume and a significant balance fluctuation on the cluster, coinciding with the time of both Atomic Wallet and CoinsPaid crypto payment gateway attacks.
2. Withdrawing the stolen money via Avalanche Bridge
In both the CoinsPaid crypto payment gateway CoinsPaid and Atomic wallet hacks, most of the stolen funds were sent in the form of USDT to the SwftSwap cryptocurrency service on the Avalanche-C blockchain. A small portion of the stolen funds was sent to the Yobit exchange.
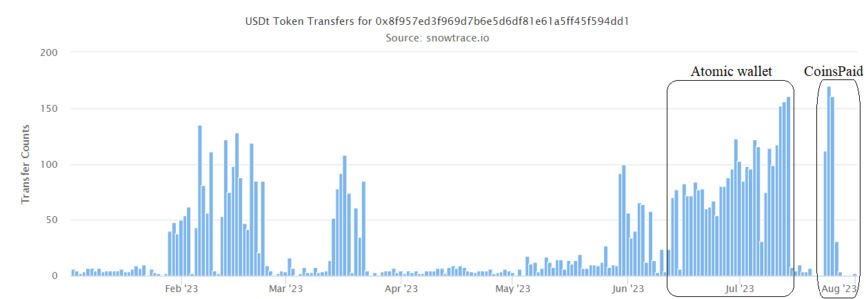
Just like the Sinbad mixer, the SwftSwap service volumes chart shows a significant increase in the number of transactions during the attacks on Atomic Wallet and CoinsPaid crypto payment gateway.
Lessons Learned from the Hack
This unfortunate incident provided some valuable experiences and insights for CoinsPaid that can help decrease both the number of crypto payment gateway hacking incidents in the crypto market and their scale of impact on the industry.
Here is the list of practical tips our security experts have compiled that other cryptocurrency and crypto payment gateway providers can implement to boost hacker protection significantly.
- Do not ignore cybersecurity incidents, i.e. attempts to break into your company’s infrastructure, social engineering, phishing, etc. This may be a sign of hackers preparing for a major attack.
- Explain to your employees how perpetrators use fake job offers, bribing, and even ask for harmless tech advice to access the company’s infrastructure and get closer to the crypto payment gateway funds.
- Implement security practices for privileged users.
- Implement the principles of Separation of Duties and Least Privilege.
- Ensure the protection of employees’ workstations.
- Keep infrastructure components of the crypto payment gateway up to date.
- Segment networks and implement authentication and encryption between infrastructure components.
- Create a separate security log store to upload all relevant events.
- Set up a monitoring and alerting system for all suspicious activity in your infrastructure and applications.
- Create an honest violator model and take measures adequate to the threats and risks that your crypto payment gateway or any business bears.
- Keep track of operating balances and monitor their unusual movement and behaviour.
- Reduce the funds available for the operation of the company to the necessary minimum.
CoinsPaid is currently planning a dedicated round-table event initiative to discuss the pressing challenges among blockchain-related companies to minimise the impact of hacking incidents. This is an important step towards creating a more secure and resilient blockchain ecosystem. We invite all blockchain industry leaders, cybersecurity companies, crypto payment gateway providers, those affected by hacks, and all related parties to participate in this discussion and help us start the change.
Let’s work together to develop innovative approaches and ensure our industry remains safe and secure. If you are interested in participating or learning more about the discussion, please reach out to CoinsPaid CMO, Eugen Kuzin, at https://www.linkedin.com/in/eugen-kuzin.